Policy and Procedures for Information Security Identity Access Management
This policy describes principles and rules for accessing UNFPA data and systems.
Policy and Procedures for Network and Cloud Security
This policy describes principles and rules for network and cloud security.
Policy for Third-party Information and Communication Technology (ICT) Risk Management
This policy describes principles and rules for standard and critical third parties providing digital services.
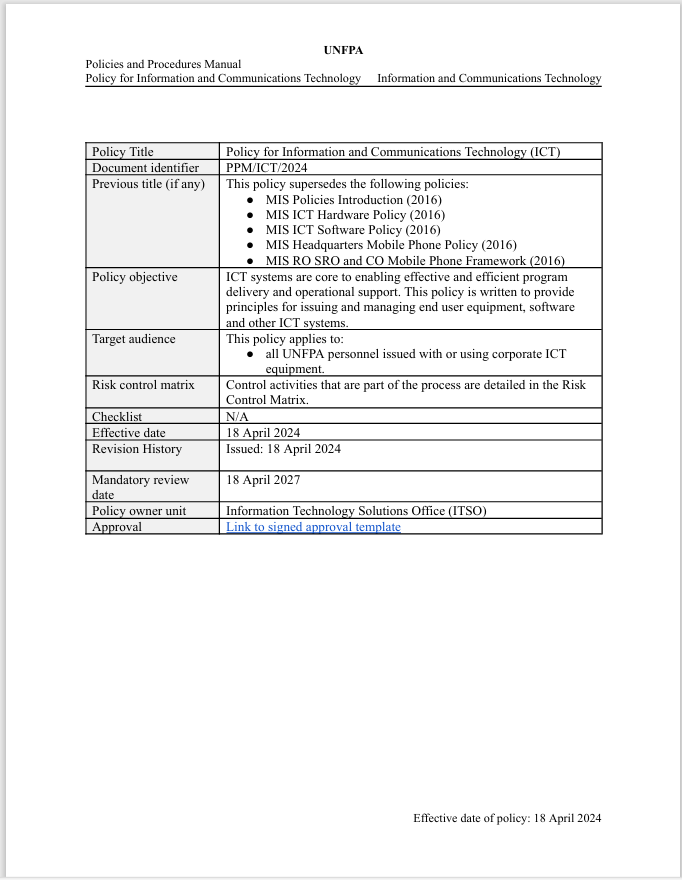
Policy for Information and Communications Technology (ICT)
Principles and procedures related to the procurement, development, issuance, use and support of end-user equipment, software and other ICT systems.
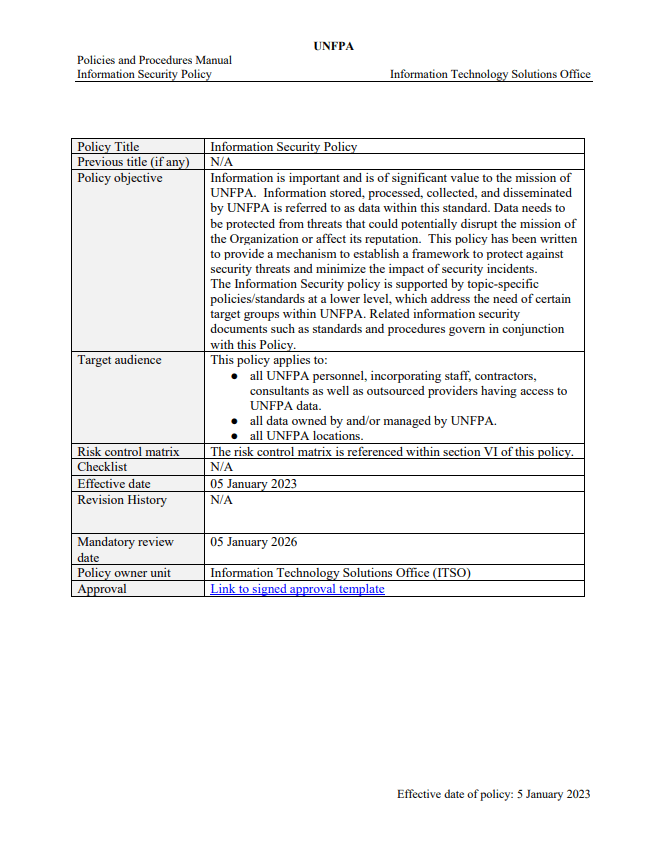
Information Security Policy
This policy recognises the value of data and provides minimum requirements to units and individuals across the organisation for security of UNFPA data. The requirements include selective controls from the ISO: IEC 27000 industry standard and is supported by a series of domain specific policies and standards that should be read in conjunction with this policy.
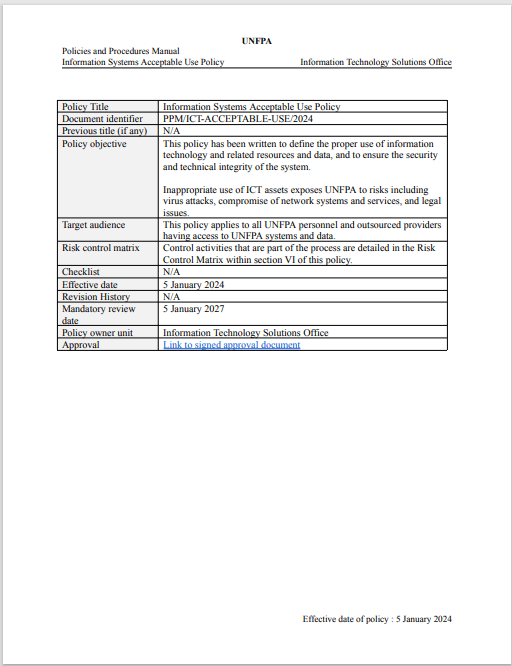
Information Systems Acceptable Use Policy
This policy defines the conditions that constitute acceptable use of UNFPA information communications and technology (ICT) systems.
Policy for UNFPA Email
This policy provides users with technical guidelines for permitted use of the UNFPA e-mail system and details how to ensure the system remains secure from unauthorized access.